- Open http://www.capturefullpage.com/.
- Enter URL(Web Page Address) you want to take screenshot
- Press Take Screenshot
- Wait for few seconds and you can can see your screenshot.
- Download or save the image file .
Pages
▼
Thursday, March 28, 2013
How Take a Full Web Page Screenshots
Wednesday, March 27, 2013
VLC Skins: Make Vlc look like quicktime, windows media player,wmp,winamp,iTunes
How to use these skins?
Skins do not work on Mac OS X!Put the downloaded VLT files in the following folder:
- On Windows: the skins folder in the VLC installation directory (e.g.C:\Program Files\VLC\skins)
- On Linux/Unix: ~/.local/share/vlc/skins2
Then open your VLC settings and change your interface from native to skins. You can choose your desired skin already there or change it when you are in the skins mode by rightclicking somewhere on the skin and going toInterface>Choose Skin.
VLC needs to be restarted to change to skins mode.
Download all the skins at once here (37MiB).
Tuesday, March 26, 2013
Request a new IP address from your ISP server
Here’s how to do it in windows:
1. Click Start
2. Click run
3. In the run box type cmd.exe and click OK
4. When the command prompt opens type the following.
1. Click Start
2. Click run
3. In the run box type cmd.exe and click OK
4. When the command prompt opens type the following.
ENTER after each new line.
ipconfig /flushdns
ipconfig /release
ipconfig /renew
exit
ipconfig /flushdns
ipconfig /release
ipconfig /renew
exit
Note: This might only work for DSL/Modem Internet Connection, not for Cable Internet users
Thursday, March 21, 2013
How to number rows in a Word table
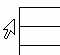
- To number rows, select the left most column in the table and click Numbering on the Formatting toolbar. To select a column, hover the mouse over the column until Word displays the selection arrow (see below) and click. In Word 2007, select the column and then click Numbering in the Paragraph group on the Home tab.
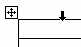
- To number columns, select the top row in the table and click Numbering on the Formatting toolbar. To select a row, hover the mouse in the left margin just next to the row you want to click. When Word displays the selection tool (see below) click to select the row. In Word 2007, select the row and then click Numbering in the Paragraph group on the Home tab.
Select a column
Select a row
In truth, you can number any row or column, but most likely, you’ll want to display numbers to the left or across the top of the table. I realize that you won’t want to number most tables and columns, but I still like knowing I can do it.
 |
| Number Rows |
 |
| Number Columns |
Wednesday, March 20, 2013
Tuesday, March 19, 2013
Computer Glossary (T-Z)
- Telnet
A way to communicate with a remote computer over a network. - Trackball
Input device that controls the position of the cursor on the screen; the unit is mounted near the keyboard, and movement is controlled by moving a ball. - Terabytes (TB)
A thousand gigabytes. - Teraflop
A measure of a computer's speed. It can be expressed as a trillion floating-point operations per second. - Trojan Horse
See virus. - UNIX.
A very powerful operating system used as the basis of many high-end computer applications. - Upload
The process of transferring information from a computer to a web site (or other remote location on a network). v. To transfer information from a computer to a web site (or other remote location on a network). - URL
Uniform Resource Locator.
1. The protocol for identifying a document on the Web.
2. A Web address (e.g., www.tutorialspoint.com). A URL is unique to each user. See also domain. - UPS
Universal Power Supply or Uninterruptible Power Supply. An electrical power supply that includes a battery to provide enough power to a computer during an outage to back-up data and properly shut down. - USB
A multiple-socket USB connecter that allows several USB-compatible devices to be connected to a computer. - USENET
A large unmoderated and unedited bulletin board on the Internet that offers thousands of forums, called newsgroups. These range from newsgroups exchanging information on scientific advances to celebrity fan clubs. - User friendly
A program or device whose use is intuitive to people with a nontechnical background. - Video teleconferencing
A remote "face-to-face chat," when two or more people using a webcam and an Internet telephone connection chat online. The webcam enables both live voice and video. - Virtual reality (VR)
A technology that allows one to experience and interact with images in a simulated three-dimensional environment. For example, you could design a room in a house on your computer and actually feel that you are walking around in it even though it was never built. (The Holodeck in the science-fiction TV series Star Trek: Voyager would be the ultimate virtual reality.) Current technology requires the user to wear a special helmet, viewing goggles, gloves, and other equipment that transmits and receives information from the computer. - Virus
An unauthorized piece of computer code attached to a computer program or portions of a computer system that secretly copies itself from one computer to another by shared discs and over telephone and cable lines. It can destroy information stored on the computer, and in extreme cases, can destroy operability. Computers can be protected from viruses if the operator utilizes good virus prevention software and keeps the virus definitions up to date. Most viruses are not programmed to spread themselves. They have to be sent to another computer by e-mail, sharing, or applications. The worm is an exception, because it is programmed to replicate itself by sending copies to other computers listed in the e-mail address book in the computer. There are many kinds of viruses, for example:
Boot viruses place some of their code in the start-up disk sector to automatically execute when booting. Therefore, when an infected machine boots, the virus loads and runs.
File viruses attached to program files (files with the extension ..exe.). When you run the infected program, the virus code executes.
Macro viruses copy their macros to templates and/or other application document files.
Trojan Horse is a malicious, security-breaking program that is disguised as something benign such as a screen saver or game.
Worm launches an application that destroys information on your hard drive. It also sends a copy of the virus to everyone in the computer's e-mail address book. - WAV
A sound format (pronounced .wave.) used to reproduce sounds on a computer. - Webcam
A video camera/computer setup that takes live images and sends them to a Web browser. - Window
A portion of a computer display used in a graphical interface that enables users to select commands by pointing to illustrations or symbols with a mouse. "Windows" is also the name Microsoft adopted for its popular operating system. - World Wide Web ("WWW" or "the Web")
A network of servers on the Internet that use hypertext-linked databases and files. It was developed in 1989 by Tim Berners-Lee, a British computer scientist, and is now the primary platform of the Internet. The feature that distinguishes the Web from other Internet applications is its ability to display graphics in addition to text. - Word processor
A computer system or program for setting, editing, revising, correcting, storing, and printing text. - Worm
See virus. - WYSIWYG
What You See Is What You Get. When using most word processors, page layout programs (See desktop publishing), and web page design programs, words and images will be displayed on the monitor as they will look on the printed page or web page.
Monday, March 18, 2013
Computer Glossary (P-S)
- Palm
A hand-held computer. - PC
Personal computer. Generally refers to computers running Windows with a Pentium processor. - PC board
Printed Circuit board. A board printed or etched with a circuit and processors. Power supplies, information storage devices, or changers are attached. - PDA
Personal Digital Assistant. A hand-held computer that can store daily appointments, phone numbers, addresses, and other important information. Most PDAs link to a desktop or laptop computer to download or upload information. - PDF
Portable Document Format. A format presented by Adobe Acrobat that allows documents to be shared over a variety of operating systems. Documents can contain words and pictures and be formatted to have electronic links to other parts of the document or to places on the web. - Pentium chip
Intel's fifth generation of sophisticated high-speed microprocessors. Pentium means .the fifth element.. - Peripheral
Any external device attached to a computer to enhance operation. Examples include external hard drive, scanner, printer, speakers, keyboard, mouse, trackball, stylus and tablet, and joystick. - Personal computer (PC)
A single-user computer containing a central processing unit (CPU) and one or more memory circuits. - Petabyte
A measure of memory or storage capacity and is approximately a thousand terabytes. - Petaflop
A theoretical measure of a computer's speed and can be expressed as a thousand-trillion floating-point operations per second. - Platform
The operating system, such as UNIX., Macintosh., Windows., on which a computer is based. - Plug and play
Computer hardware or peripherals that come set up with necessary software so that when attached to a computer, they are .recognized. by the computer and are ready to use. - Pop-up menu
A menu window that opens vertically or horizontally on-screen to display context-related options. Also called drop-down menu or pull-down menu. - Power PC
A competitor of the Pentium chip. It is a new generation of powerful sophisticated microprocessors produced from an Apple-IBM-Motorola alliance. - Printer
A mechanical device for printing a computer's output on paper. There are three major types of printers: Dot matrix: creates individual letters, made up of a series of tiny ink dots, by punching a ribbon with the ends of tiny wires. (This type of printer is most often used in industrial settings, such as direct mail for labeling.)
Ink jet: sprays tiny droplets of ink particles onto paper.
Laser: uses a beam of light to reproduce the image of each page using a magnetic charge that attracts dry toner that is transferred to paper and sealed with heat. - Program
A precise series of instructions written in a computer language that tells the computer what to do and how to do it. Programs are also called .software. or .applications. - Programming language
A series of instructions written by a programmer according to a given set of rules or conventions (.syntax.). High-level programming languages are independent of the device on which the application (or program) will eventually run; low-level languages are specific to each program or platform. Programming language instructions are converted into programs in language specific to a particular machine or operating system (.machine language.) so that the computer can interpret and carry out the instructions. Some common programming languages are BASIC, C, C++, dBASE, FORTRAN, and Perl. - Puck
An input device, like a mouse. It has a magnifying glass with crosshairs on the front of it that allows the operator to position it precisely when tracing a drawing for use with CAD-CAM software. - Pull-down menu
A menu window that opens vertically on-screen to display context-related options. Also called drop-down menu or pop-up menu. - Push technology
Internet tool that delivers specific information directly to a user's desktop, eliminating the need to surf for it. PointCast, which delivers news in user-defined categories, is a popular example of this technology. - QuickTime.
Audio-visual software that allows movie-delivery via the Internet and e-mail. QuickTime mages are viewed on a monitor. - RAID
Redundant Array of Inexpensive Disks. A method of spreading information across several disks set up to act as a unit, using two different techniques:
Disk striping: storing a bit of information across several discs (instead of storing it all on one disc and hoping that the disc doesn't crash).
Disk mirroring: simultaneously storing a copy of information on another disc so that the information can be recovered if the main disc crashes. - RAM
Random Access Memory. One of two basic types of memory. Portions of programs are stored in RAM when the program is launched so that the program will run faster. Though a PC has a fixed amount of RAM, only portions of it will be accessed by the computer at any given time. Also called memory. - Right-click
Using the right mouse button to open context-sensitive drop-down menus. - ROM
Read-Only Memory. One of two basic types of memory. ROM contains only permanent information put there by the manufacturer. Information in ROM cannot be altered, nor can the memory be dynamically allocated by the computer or its operator. - Scanner
An electronic device that uses light-sensing equipment to scan paper images such as text, photos, and illustrations and translate the images into signals that the computer can then store, modify, or distribute. - Search engine
Software that makes it possible to look for and retrieve material on the Internet, particularly the Web. Some popular search engines are Alta Vista, Google, HotBot, Yahoo!, Web Crawler, and Lycos. - Server
A computer that shares its resources and information with other computers, called clients, on a network. - Shareware
Software created by people who are willing to sell it at low cost or no cost for the gratification of sharing. It may be freestanding software, or it may add functionality to existing software. - Software
Computer programs; also called .applications. - Spider
A process search engines use to investigate new pages on a web site and collect the information that needs to be put in their indices. - Spreadsheet
Software that allows one to calculate numbers in a format that is similar to pages in a conventional ledger. - Storage
Devices used to store massive amounts of information so that it can be readily retrieved. Devices include RAIDs, CD-ROMs, DVDs - Streaming
Taking packets of information (sound or visual) from the Internet and storing it in temporary files to allow it to play in continuous flow. - Stylus and tablet
A input device similar to a mouse. The stylus is pen shaped. It is used to .draw. on a tablet (like drawing on paper) and the tablet transfers the information to the computer. The tablet responds to pressure.the firmer the pressure used to draw, the thicker the line appears. - Surfing
Exploring the Internet. - Surge protector
A controller to protect the computer and make up for variances in voltage.
Sunday, March 17, 2013
Computer Glossary (L-O)
- Linux
A UNIX.-like, open-source operating system developed primarily by Linus Torvalds. Linux is free and runs on many platforms, including both PCs and Macintoshes. Linux is an open-source operating system, meaning that the source code of the operating system is freely available to the public. Programmers may redistribute and modify the code, as long as they don't collect royalties on their work or deny access to their code. Since development is not restricted to a single corporation more programmers can debug and improve the source code faster. - Laptop and notebook
Small, lightweight, portable battery-powered computers that can fit onto your lap. They each have a thin, flat, liquid crystal display screen. - Macro
A script that operates a series of commands to perform a function. It is set up to automate repetitive tasks. - Mac OS
An operating system with a graphical user interface, developed by Apple. for Macintosh. computers. Current System .X.1. (10) combines the traditional Mac interface with a strong underlying UNIX. operating system for increased performance and stability. - Megabyte (MB)
Equal to 1,048,576 bytes, usually rounded off to one million bytes (also called a .meg.). - Memory
Temporary storage for information, including applications and documents. The information must be stored to a permanent device, such as a hard disc or CD-ROM before the power is turned off, or the information will be lost. Computer memory is measured in terms of the amount of information it can store, commonly in megabytes or gigabytes. - Menu
A context-related list of options that users can choose from. - Menu bar
The horizontal strip across the top of an application's window. Each word on the strip has a context sensitive drop-down menu containing features and actions that are available for the application in use. - Merge
To combine two or more files into a single file. - MHz
An abbreviation for Megahertz, or one million hertz. One MHz represents one million clock cycles per second and is the measure of a computer microprocessor's speed. For example, a microprocessor that runs at 300 MHz executes 300 million cycles per second. Each instruction a computer receives takes a fixed number of clock cycles to carry out, therefore the more cycles a computer can execute per second, the faster its programs run. Megahertz is also a unit of measure for bandwidth. - Microprocessor
A complete central processing unit (CPU) contained on a single silicon chip. - Minimize
A term used in a GUI operating system that uses windows. It refers to reducing a window to an icon, or a label at the bottom of the screen, allowing another window to be viewed. - Modem
A device that connects two computers together over a telephone or cable line by converting the computer's data into an audio signal. Modem is a contraction for the process it performs: modulate-demodulate. - Monitor
A video display terminal. - Mouse
A small hand-held device, similar to a trackball, used to control the position of the cursor on the video display; movements of the mouse on a desktop correspond to movements of the cursor on the screen. - MP3
Compact audio and video file format. The small size of the files makes them easy to download and e-mail. Format used in portable playback devices. - Multimedia
Software programs that combine text and graphics with sound, video, and animation. A multimedia PC contains the hardware to support these capabilities. - MS-DOS
An early operating system developed by Microsoft Corporation (Microsoft Disc Operating System). - Network
A system of interconnected computers. - Open source
Computer programs whose original source code was revealed to the general public so that it could be developed openly. Software licensed as open source can be freely changed or adapted to new uses, meaning that the source code of the operating system is freely available to the public. Programmers may redistribute and modify the code, as long as they don't collect royalties on their work or deny access to their code. Since development is not restricted to a single corporation more programmers can debug and improve the source code faster. - Operating system
A set of instructions that tell a computer on how to operate when it is turned on. It sets up a filing system to store files and tells the computer how to display information on a video display. Most PC operating systems are DOS (disc operated system) systems, meaning the instructions are stored on a disc (as opposed to being originally stored in the microprocessors of the computer). Other well-known operating systems include UNIX, Linux, Macintosh, and Windows. - Output
Data that come out of a computer device. For example, information displayed on the monitor, sound from the speakers, and information printed to paper.
Saturday, March 16, 2013
Computer Glossary (G-k)
- Gigabyte (GB)
1024 megabytes. Also called gig. - Glitch
The cause of an unexpected malfunction. - Gopher
An Internet search tool that allows users to access textual information through a series of menus, or if using FTP, through downloads. - GUI
Graphical User Interface. A system that simplifies selecting computer commands by enabling the user to point to symbols or illustrations (called icons) on the computer screen with a mouse. - Groupware
Software that allows networked individuals to form groups and collaborate on documents, programs, or databases. - Hacker
A person with technical expertise who experiments with computer systems to determine how to develop additional features. Hackers are occasionally requested by system administrators to try and .break into. systems via a network to test security. The term hacker is sometimes incorrectly used interchangeably with cracker. A hacker is called a .white hat. and a cracker a .black hat. - Hard copy
A paper printout of what you have prepared on the computer. - Hard drive
Another name for the hard disc that stores information information in a computer. - Hardware
The physical and mechanical components of a computer system, such as the electronic circuitry, chips, monitor, disks, disk drives, keyboard, modem, and printer. - Home page
The main page of a Web site used to greet visitors, provide information about the site, or to direct the viewer to other pages on the site. - HTML
Hypertext Markup Language. A standard of text markup conventions used for documents on the World Wide Web. Browsers interpret the codes to give the text structure and formatting (such as bold, blue, or italic). - HTTP
Hypertext Transfer Protocol. A common system used to request and send HTML documents on the World Wide Web. It is the first portion of all URL addresses on the World Wide Web - HTTPS
Hypertext Transfer Protocol Secure. Often used in intracompany internet sites. Passwords are required to gain access. - Hyperlink
Text or an image that is connected by hypertext coding to a different location. By selecting the text or image with a mouse, the computer .jumps to. (or displays) the linked text. - Hypermedia
Integrates audio, graphics, and/or video through links embedded in the main program. - Hypertext
A system for organizing text through links, as opposed to a menu-driven hierarchy such as Gopher. Most Web pages include hypertext links to other pages at that site, or to other sites on the World Wide Web. - Icons
Symbols or illustrations appearing on the computer screen that indicate program files or other computer functions. - Input
Data that goes into a computer device. - Input device
A device, such as a keyboard, stylus and tablet, mouse, puck, or microphone, that allows input of information (letters, numbers, sound, video) to a computer. - Instant messenging (IM)
A chat application that allows two or more people to communicate over the Internet via real-time keyed-in messages. - Interface
The interconnections that allow a device, a program, or a person to interact. Hardware interfaces are the cables that connect the device to its power source and to other devices. Software interfaces allow the program to communicate with other programs (such as the operating system), and user interfaces allow the user to communicate with the program (e.g., via mouse, menu commands, icons, voice commands, etc.). - Internet
An international conglomeration of interconnected computer networks. Begun in the late 1960s, it was developed in the 1970s to allow government and university researchers to share information. The Internet is not controlled by any single group or organization. Its original focus was research and communications, but it continues to expand, offering a wide array of resources for business and home users. - IP (Internet Protocol) address
An Internet Protocol address is a unique set of numbers used to locate another computer on a network. The format of an IP address is a 32-bit string of four numbers separated by periods. Each number can be from 0 to 255 (i.e., 1.154.10.266). Within a closed network IP addresses may be assigned at random, however, IP addresses of web servers must be registered to avoid duplicates. - Java
An object-oriented programming language designed specifically for programs (particularly multimedia) to be used over the Internet. Java allows programmers to create small programs or applications (applets) to enhance Web sites. - Javascript/ECMA script
A programming language used almost exclusively to manipulate content on a web page. Common Javascript functions include validating forms on a web page, creating dynamic page navigation menus, and image rollovers. - kilobyte (K or KB)
Equal to 1,024 bytes.
Friday, March 15, 2013
Computer Glossary (D-F)
- Database
A collection of similar information stored in a file, such as a database of addresses. This information may be created and stored in a database management system (DBMS). - Debug
Slang. To find and correct equipment defects or program malfunctions. - Default
The pre-defined configuration of a system or an application. In most programs, the defaults can be changed to reflect personal preferences. - Desktop
The main directory of the user interface. Desktops usually contain icons that represent links to the hard drive, a network (if there is one), and a trash or recycling can for files to be deleted. It can also display icons of frequently used applications, as requested by the user. - Desktop publishing
The production of publication-quality documents using a personal computer in combination with text, graphics, and page layout programs. - Directory
A repository where all files are kept on computer. - Disk
Two distinct types. The names refer to the media inside the container:
A hard disc stores vast amounts of data. It is usually inside the computer but can be a separate peripheral on the outside. Hard discs are made up of several rigid coated metal discs. Currently, hard discs can store 15 to 30 Gb (gigabytes)
A floppy disc, 3.5" square, usually inserted into the computer and can store about 1.4 megabytes of data. The 3.5" square .floppies. have a very thin, flexible disc inside. There is also an intermediate-sized floppy disc, trademarked Zip discs, which can store 250 megabytes of data. - Disk drive
The equipment that operates a hard or floppy disc. - Domain
Represents an IP (Internet Protocol) address or set of IP addresses that comprise a domain. The domain name appears in URLs to identify web pages or in email addresses. For example, the email address for the First Lady is first.lady@whitehouse.gov, .whitehouse.gov. being the domain name. Each domain name ends with a suffix that indicates what .top level domain. it belongs to. These are: ..com. for commercial, ..gov. for government, ..org. for organization, ..edu. for educational institution, ..biz. for business, ..info. for information, ..tv. for television, ..ws. for website. Domain suffixes may also indicate the country in which the domain is registered. No two parties can ever hold the same domain name. - Domain name
The name of a network or computer linked to the Internet. Domains are defined by a common IP address or set of similar IP (Internet Protocol) addresses. - Download
The process of transferring information from a web site (or other remote location on a network) to the computer. It is possible to .download a file. or .view a download. - DOS
Disk Operating System. An operating system designed for early IBM-compatible PCs. - Drop-down menu
A menu window that opens vertically on-screen to display context-related options. Also called pop-up menu or pull-down menu. - DSL
Digital Subscriber Line. A method of connecting to the Internet via a phone line. A DSL connection uses copper telephone lines but is able to relay data at much higher speeds than modems and does not interfere with telephone use. - DVD
Digital Video Disc.Similar to a CD-ROM, it stores and plays both audio and video. - E-book
An electronic (usually hand-held) reading device that allows a person to view digitally stored reading materials. - Email
Electronic mail; messages, including memos or letters, sent electronically between networked computers that may be across the office or around the world. - Emoticon
A text-based expression of emotion created from ASCII characters that mimics a facial expression when viewed with your head tilted to the left. Here are some examples:
:-) Smiling
:-( Frowning
;-) Winking
:_( Crying - Encryption
The process of transmitting scrambled data so that only authorized recipients can unscramble it. For instance, encryption is used to scramble credit card information when purchases are made over the Internet. - Ethernet
A type of network. - Ethernet card
A board inside a computer to which a network cable can be attached. - File
A set of data that is stored in the computer. - Firewall
A set of security programs that protect a computer from outside interference or access via the Internet. - Folder
A structure for containing electronic files. In some operating systems, it is called a .directory. - Fonts
Sets of typefaces (or characters) that come in different styles and sizes. - Freeware
Software created by people who are willing to give it away for the satisfaction of sharing or knowing they helped to simplify other people's lives. It may be freestanding software, or it may add functionality to existing software. - FTP
File Transfer Protocol. A format and set of rules for transferring files from a host to a remote computer.
Thursday, March 14, 2013
Computer Glossary (A-C)
- Applet
A small Java application that is downloaded by an ActiveX or Java-enabled web browser. Once it has been downloaded, the applet will run on the user's computer. Common applets include financial calculators and web drawing programs. - Application
Computer software that performs a task or set of tasks, such as word processing or drawing. Applications are also referred to as programs. - ASCII
American Standard Code for Information Interchange, an encoding system for converting keyboard characters and instructions into the binary number code that the computer understands. - Bandwidth
The capacity of a networked connection. Bandwidth determines how much data can be sent along the networked wires. Bandwidth is particularly important for Internet connections, since greater bandwidth also means faster downloads. - Binary code
The most basic language a computer understands, it is composed of a series of 0s and 1s. The computer interprets the code to form numbers, letters, punctuation marks, and symbols. - Bit
The smallest piece of computer information, either the number 0 or 1. In short ther are called binary digits. - Boot
To start up a computer. Cold boot.restarting computer after having turned off the power. Warm boot.restarting computer without having turned off the power. - Browser
Software used to navigate the Internet. Netscape Navigator and Microsoft Internet Explorer are today's most popular browsers for accessing the World Wide Web. - Bug
A malfunction due to an error in the program or a defect in the equipment. - Byte
Most computers use combinations of eight bits, called bytes, to represent one character of data or instructions. For example, the word .cat. has three characters, and it would be represented by three bytes. - Cache
A small data-memory storage area that a computer can use to instantly re-access data instead of re-reading the data from the original source, such as a hard drive. Browsers use a cache to store web pages so that the user may view them again without reconnecting to the Web. - CAD-CAM
Computer Aided Drawing-Computer Aided Manufacturing. The instructions stored in a computer that will be translated to very precise operating instructions to a robot, such as for assembling cars or laser-cutting signage. - CD-ROM
Compact Disc Read-Only Memory. An optically read disc designed to hold information such as music, reference materials, or computer software. A single CD-ROM can hold around 640 megabytes of data, enough for several encyclopedias. Most software programs are now delivered on CD-ROMs. - CGI
Common Gateway Interface. A programming standard that allows visitors to fill out form fields on a Web page and have that information interact with a database, possibly coming back to the user as another Web page. CGI may also refer to Computer-Generated Imaging, the process in which sophisticated computer programs create still and animated graphics, such as special effects for movies. - Chat
Typing text into a message box on a screen to engage in dialog with one or more people via the Internet or other network. - Chip
A tiny wafer of silicon containing miniature electric circuits that can store millions of bits of information. - Client
A single user of a network application that is operated from a server. A client/server architecture allows many people to use the same data simultaneously. The program's main component (the data) resides on a centralized server, with smaller components (user interface) on each client. - Cookie
A text file sent by a Web server that is stored on the hard drive of a computer and relays back to the Web server things about the user, his or her computer, and/or his or her computer activities. - CPU
Central Processing Unit. The brain of the computer. - Cracker
A person who .breaks in. to a computer through a network, without authorization and with mischievous or destructive intent. - Crash
A hardware or software problem that causes information to be lost or the computer to malfunction. Sometimes a crash can cause permanent damage to a computer. - Cursor
A moving position-indicator displayed on a computer monitor that shows a computer operator where the next action or operation will take place. - Cyberspace
Slang for internet ie. An international conglomeration of interconnected computer networks. Begun in the late 1960s, it was developed in the 1970s to allow government and university researchers to share information. The Internet is not controlled by any single group or organization. Its original focus was research and communications, but it continues to expand, offering a wide array of resources for business and home users.
Tuesday, March 12, 2013
Use Chrome commands
Use the chrome:// commands to access many hidden features of Chrome. There is a few dozen of these commands available that will allow you to do everything from viewing DNS information, GPU information, look for conflicts, setting flags, and much more. A listing of these commands can be accessed by typing chrome://chrome-urls in the Omnibox.
Use the Omnibox to do more than just search
The Google Omnibox does more than displaying the URL and allowing you to search. It is also capable of performing mathematical calculations (as shown in the picture) and even answer questions such as "how many cups are in 2 liters?" Try adding any math calculation now in the Omnibox without pressing enter to have the results shown.


Monday, March 11, 2013
Google Chrome keyboard shortcuts
Like any good browser, Google Chrome has several dozen different keyboard shortcuts that can help improve your productivity. Below is just a few of our top favorites.
Ctrl + 1-8 = Pressing Ctrl and any number 1 through 8 will move to the corresponding tab in your tab bar.
Ctrl + 9 = Switch to the last tab.
Ctrl + H = Show history
Ctrl + J = Open Downloads window
Ctrl + K = Move the cursor to the Omnibox (address bar)
Ctrl + T = Open a new tab
Ctrl + 9 = Switch to the last tab.
Ctrl + H = Show history
Ctrl + J = Open Downloads window
Ctrl + K = Move the cursor to the Omnibox (address bar)
Ctrl + T = Open a new tab
Remove formatting in Word from any pasted text.
When copying text from another document or Internet web page and pasting it into Microsoft Word, Word will keep the formatting of the text. For example, if you were to copy the text on this page to a Word file, this text would remain bold, and this text would remain blue. To remove the formatting in Microsoft Word from any text highlight the text and press the shortcut key Ctrl + Space-bar This will set the text to the default font, remove the formatting, and even remove links.
Alternatively you can use the Paste Special option or Keep Text Only option in Microsoft Word to paste the text with no formatting.
Bonus Tip: In most versions of Windows Ctrl + Windows Key + V will also often paste text as plain text.
Sunday, March 10, 2013
Windows 8 keyboard shortcuts
Knowing at least some of the Windows 8 keyboard shortcuts will make your Windows 8 experience much more enjoyable. Try to memorize these top Windows 8 shortcut keys.
Press the Windows key to open the Start screen or switch to the Desktop (if open).
Press the Windows key + D will open the Windows Desktop.
Press the Windows key + . to pin and unpin Windows apps on the side of the screen.
Press the Windows key + X to open the power user menu, which gives you access to many of the features most power users would want (e.g. Device Manager and Command Prompt).
Press the Windows key + C to open the Charms.
Press the Windows key + I to open the Settings, which is the same Settings found in Charms.
Press and hold the Windows key + Tab to show open apps.
Press the Windows key + Print screen to create a screen shot, which is automatically saved into your My Pictures folder.
Thursday, March 7, 2013
Windows 8: How to Create a New Hard Drive Partition

Disk partitioning is essentially separating the hard disk into different sections or parts for storage. If you want to try a new operating system without overwriting your main Windows drive, you can do this partitioning the hard drive.
Partitioning the hard disk also makes it possible to multiboot different operating systems. In addition to creating multiboot configurations, you can also use partitions as extra storage mediums for specific files or for backing up important files.
Benefits of Having Another Partition:
- Backup System Files
- Install multiple Operating Systems
- Extend the functionality of the hard drive
- Improve security (you can use the other partition in case one fails)
Creating a Partition on Windows 8
Hold the Windows logo key on your keyboard and press “R” (Winkey+R). This will launch the Run the utility. Type “diskmgmt.msc” inside the text box and press Enter. This will open the Windows Disk Management utility. This is where you can format, create, and delete hard drive partitions.
In order to create a partition, you need unallocated space. Unallocated space is basically disk space that is not formatted or not prepared for storage. Formatting is the act of preparing a disk space for storage. It similar to building a foundation for a place to be inhabited. Thus, unallocated space is just useless blank space with no “foundation” or format.
To create unallocated space, you need to shrink your hard drive. When you shrink your hard disk, the remaining space becomes unallocated.
To do this, right-click your main drive and select “Shrink Volume.”

Now you need to enter the amount you want to shrink the hard disk by in megabytes (1000 megabytes = 1 gigabyte). For example if you want to create a 1 gigabyte partition, enter 1,000 megabytes in the text box. Now click “Shrink.”
The Disk Management Utility will show you the maximum amount of shrink space available. That’s the maximum size that can be allocated to the new partition.

You will then see the region of unallocated space (shaded black). Remember, this space is not yet usable.

Now you need to create “foundation” or format for the unallocated space. This will allow for the space to become usable.
Right-click the region of unallocated space and select “New Simple Volume.”

This will launch the New Simple Volume Wizard. This will guide you through the installation process.

Assign the disk a drive letter. You can choose any drive letter that is not currently in use.

Select a file system for the disk. The file system is basically the type of format or “foundation” the storage device has. If you plan on installing a Windows OS to the partition select the “NTFS” file system.

Name the partition in the “Volume Label” text box. You can choose any name for your partition. As you can see, we’ve name ours “Vikitech.”

Now click “Finish” to create the new partition.

As you can see, this is the new partition that was just created.


