Leap Motion's not the household name Kinect is, but it should be — the company's motion-tracking system is more powerful, more accurate, smaller, cheaper, and just more impressive. Leap CTO David Holz came by the Verge's New York offices to give us a demo of the company's upcoming product (called The Leap), and suffice to say we're only begrudgingly returning to our mice and keyboards.
The Leap uses a number of camera sensors to map out a workspace of sorts — it's a 3D space in which you operate as you normally would, with almost none of the Kinect's angle and distance restrictions. Currently the Leap uses VGA camera sensors, and the workspace is about three cubic feet; Holz told us that bigger, better sensors are the only thing required to make that number more like thirty feet, or three hundred. Leap's device tracks all movement inside its force field, and is remarkably accurate, down to 0.01mm. It tracks your fingers individually, and knows the difference between your fingers and the pencil you're holding between two of them.
Holz showed off a number of different use cases for Leap Motion's technology. The simplest thing it can do is simulate a touch screen, so you can interact with any display as if it were touch-enabled — we were slicing pineapples in Fruit Ninja in seconds, without a moment of extra development or additional software.
Developers that do take advantage of the Leap's SDK will be able to do much more, however, and the possibilities appear to be limited only by your imagination. All kinds of different apps are being developed: some could improving remote surgery, others allow easier navigation through complex models and data, and others might put you square in the middle of a first-person shooter. It's like holding the Mario Kart steering wheel, but on a whole new level.
ather than mapping particular gestures (cross your arms to close the app, draw a circle to open a new window), Holz said developers are being encouraged to provide constant dynamic feedback. No one needed to be taught what pinch-to-zoom meant — it's the natural thing to try and do on a touchscreen, and as soon as you start pinching or spreading it becomes clear what happens. That's the paradigm for the Leap, Holz says: you should always be able to just do something, and the app or device should respond.
Leap Motion's plans are huge (Holz mentioned a few times wanting to totally upend traditional computing methods) but the company's playing its cards close. The Leap will cost $70 when it's released — sometime between December and February — and Leap Motion is also working with OEMs to embed its technology into devices. The Leap is about the size of a USB drive, but Holz says it could easily be no larger than a dime, so adding it to a laptop or tablet shouldn't be difficult.
Developers are apparently beating down the company's doors for access to the technology — Holz said thousands of Leaps will be given away in the next few months, before it's released to the public. That's no surprise: after only a few minutes of cutting fruit, scrolling around maps and webpages, and navigating through huge 3D spaces, all without ever touching a thing, we're pretty sure we've seen the next big thing in computing.
The natural comparison to any motion control is Minority Report, an imagined future everyone seems to desperately want to come true. We asked Holz about the comparison, and if Leap Motion's technology meant we'd all have Tom Cruise's awesome PreCrime dashboard in the future.
"No," he told us. "It'll be even better."




























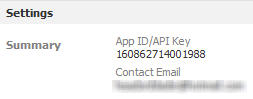 You can find your API key by opening the app settings from Facebook developers page. Replace the your-app-ID above with the app ID you just copied and follow the link. You will see options for adding the app or the canvas to your pages.
You can find your API key by opening the app settings from Facebook developers page. Replace the your-app-ID above with the app ID you just copied and follow the link. You will see options for adding the app or the canvas to your pages.