




Note that Your email address will match your public username, for example:
Profile: facebook.com/username
Then your email address will be:
Email: username@facebook.com
If you don’t have a username, you can follow the under given link and get you username.

Press the following on your mobile *#06# to see your Phone’s IMEI number(serial number).
Then check the 7th and 8th numbers
Phone serial no. x x x x x x ? ? x x x x x x x
IF the Seventh & Eighth digits of your cell phone are 02 or 20 this means your cell phone was assembled in Emirates which is very Bad quality
IF the Seventh & Eighth digits of your cell phone are 08 or 80 this means your cell phone was manufactured in Germany which is fair quality
IF the Seventh & Eighth digits of your cell phone are 01 or 10 this means your cell phone was manufactured in Finland which is very Good
IF the Seventh & Eighth digits of your cell phone are 00 this means your cell phone was manufactured in original factory which is the best Mobile Quality
IF the Seventh & Eighth digits of your cell phone are 13 this means your cell phone was assembled in Azerbaijan which is very Bad quality and also dangerous for your health.
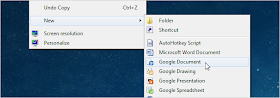
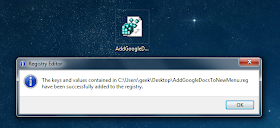
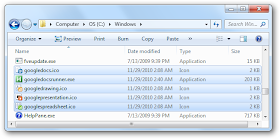
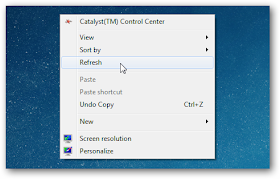

Many computer users’ wants to pretend that they are a dangerous hacker with the ability to take down any PC, and after you read this article, you can do show off your skills with nothing more than Notepad.
Of course, we’re not making an actual virus—it’s a fake virus. In fact, it’s a test virus. But it’s still fun.
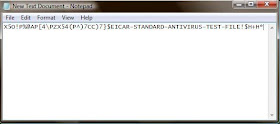
Create a Fake Virus with Notepad
Open up a Notepad window, paste in the following text, and then save it.
X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*
It should look exactly like this once you’ve pasted it.
 Text2Mail 1.1.0 requires Mac OS X version 10.5 or later. It also requires Text Editor and Mail. Text2Mail 1.1.0 is available at a price of $11.95 USD. You can download the free trial version of Text2Mail 1.1.0 from here. Stay tuned with us for more updates.
Text2Mail 1.1.0 requires Mac OS X version 10.5 or later. It also requires Text Editor and Mail. Text2Mail 1.1.0 is available at a price of $11.95 USD. You can download the free trial version of Text2Mail 1.1.0 from here. Stay tuned with us for more updates.

British police have uncovered a biggest criminal website in the history of cyber crime. Thousand of criminals were logging onto the "cyber supermarket" to shop for stolen credit card details, to learn how to manufacture illegal drugs and to even learn how to make bombs. This website (GhostMarket) worked on the strategy of stealing important and confidential information (including pin codes and passwords) of innocent net bankers and online shoppers and selling them to its members.